 |
Leosac
0.8.0
Open Source Access Control
|
 |
Leosac
0.8.0
Open Source Access Control
|
Explain how the authentication and authorization subsystem works.
In an access control system, the authentication & authorization subsystem is complex. This page aims to explain how it works in Leosac.
The task of reading credentials, validating them and taking action (opening doors) is split over multiple module. This gives us more flexibility and helps keeping the code clear and relatively simple.
Below is a diagram that illustrate how thing works:
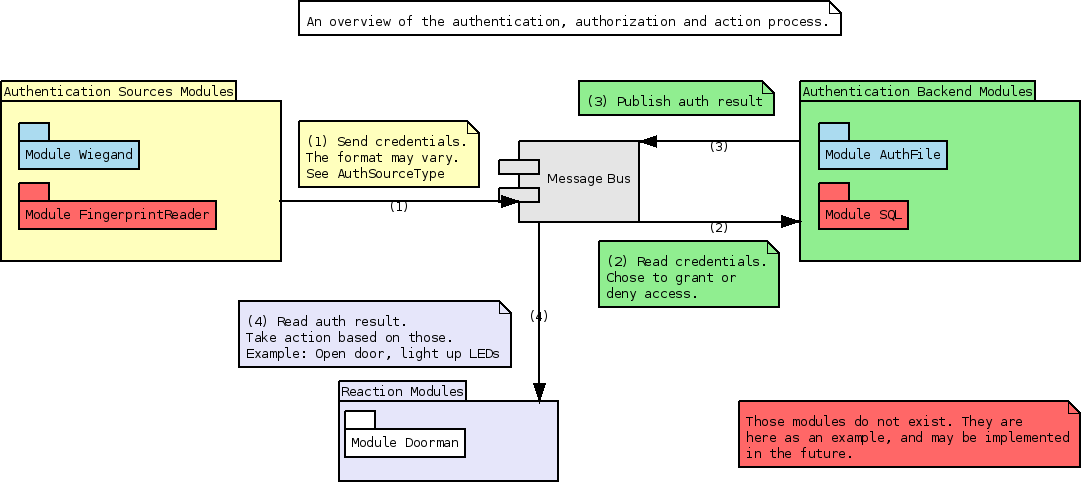
We break down the authentication & authorization code in multiple parts. There are two kinds of modules:
An authentication source module provides user-data to the system, for example a card id or a pin code. Theses modules are first in the chain of event that lead to an access control.
An authentication shall have at least one property: a name. This name will be used throughout the application to determine what device (or authentication source) triggered the events.
TODO: Also we need something to identify the [type](ref auth_data_type) of the data. (pin vs pin/card id vs card id vs ...)
An authentication backend module gather event from authentication source and check their own backend to build a profile (raw files, database, remote webservices, ...)
The profile is built by checking group-membership, credentials mapping, etc. The newly built profile is then queried to determine whether or not the user should be granted access.
In order for this to work properly, we need a decent message passing specifications.
Data type information helps authentication backends understand messages from authentication sources. It is an enumeration value, see AuthSourceType.
Currently we are lucky, we only define a few.
Understand the application message bus first.
First, a few assumptions. Authentication data from auth source may vary widely. Consider a simple pin code versus a wiegand card id. The wiegand card must holds 2 data: the value, and the number of meaningful bits. A wiegand reader can also handle PIN code + card id, augmenting complexity of the auth data.
Auth backend must be able to distinguish between those to handles them properly.
Workflow for an authentication source module:
S_.As an example, consider a message from the wiegand module, named MY_WIEGAND_1:
| Frame | Content | Type |
|---|---|---|
| 1 | "MY_WIEGAND_1" | string |
| 2 | Leosac::Auth::SourceType::SIMPLE_WIEGAND | AuthSourceType (uint8_t) |
| 3 | "12:af:cd:21" | string |
| 4 | 26 | int |
A second example for the WIEGAND_PIN auth source mode:
| Frame | Content | Type |
|---|---|---|
| 1 | "MY_WIEGAND_1" | string |
| 2 | Leosac::Auth::SourceType::WIEGAND_PIN | AuthSourceType (uint8_t) |
| 3 | "1234591" | string |
Workflow for an authentication backend module:
S_{AUTH_INSTANCE_NAME}.| Frame | Content | Type |
|---|---|---|
| 1 | "S_MY_AUTH_SOURCE_1" | string |
| 2 | Leosac::Auth::AccessStatus::Granted | AccessStatus (uint8_t) |